House of Einherjar
Review Notes on House of Einherjar
House of Einherjar
Introduction
- This exploit technique allows us to use
mallocto return a chunk at an almost arbitrary address withinav->system_memlimits. - We exploit the
malloc_consolidatefeature here.
Code Review
1
2
3
4
5
6
7
8
9
10
/* Consolidate backward. */
if (!prev_inuse(p))
{
INTERNAL_SIZE_T prevsize = prev_size (p);
size += prevsize;
p = chunk_at_offset(p, -((long) prevsize));
if (__glibc_unlikely (chunksize(p) != prevsize))
malloc_printerr ("corrupted size vs. prev_size while consolidating");
unlink_chunk (av, p);
}
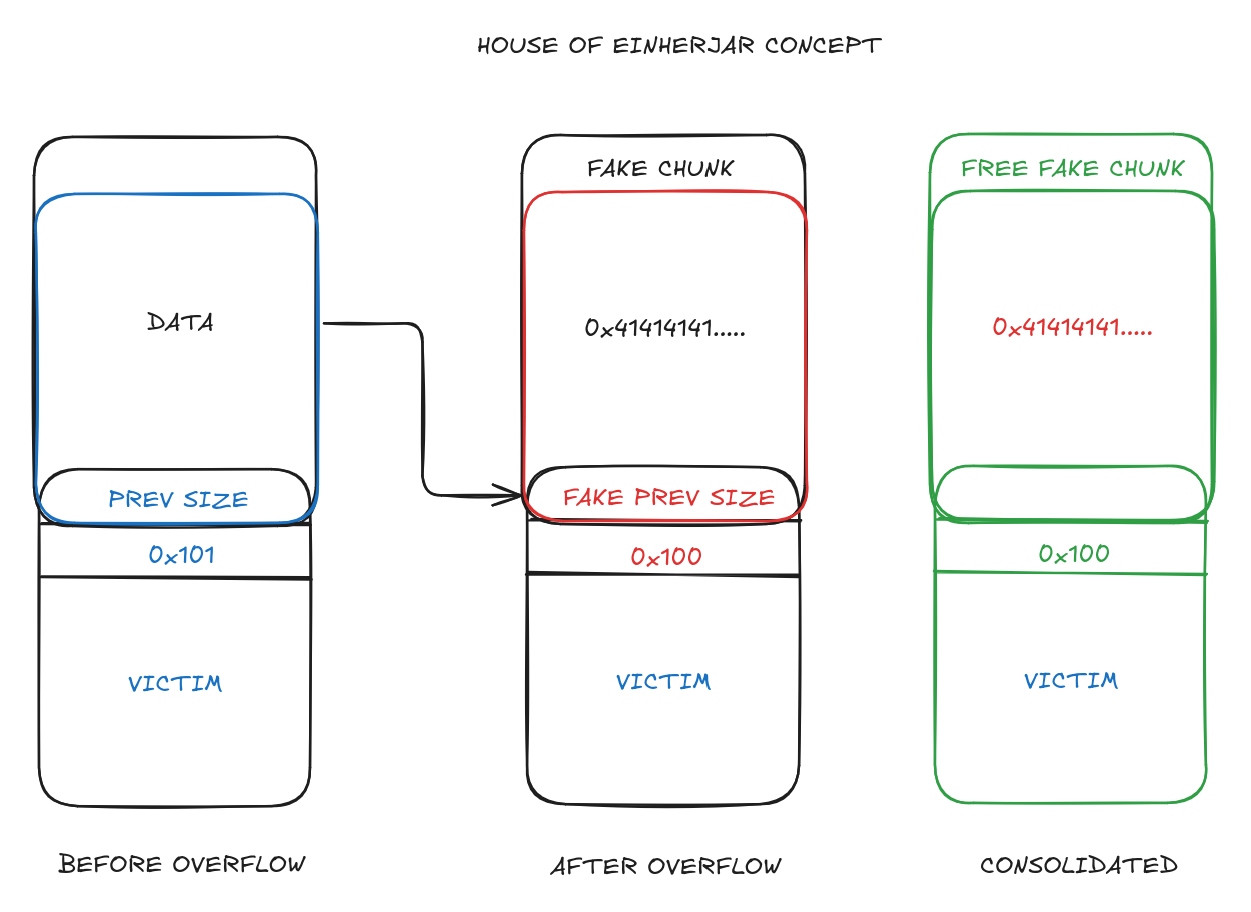
- When
mallocis called it consolidates any continuous free chunk sequences within the free list. - It checks whether the
PREV_INUSEbit is set to ascertain whether the previous chunk is allocated or not. - If the
PREV_INUSEbit is not set, it reads thePREV_SIZEfield to get the previous chunks size and adds it to the current chunk’s size. - The pointer to be returned is obtained by subtracting the previous chunk’s size from the current chunk’s address.
- The following check takes place - *Check if size of previous chunk and prevsize(p) match
(chunksize(p) != prevsize)elsecorrupted size vs. prev_size while consolidating. - The
unlink_chunkfunction is called to unlink the chunk from the free list. - This also entails the check for whether the
bk->fdandfd->bkpointers point to the current chunk.
Exploitation
- Using an off-by-one write we can set the
PREV_INUSEbit of the next chunk to 0. - We craft a fake chunk where we want the fake chunk pointer to be by setting the size of the chunk followed by the
fdandbkpointing to the fake chunk. - The
fdandbkpoints to the fake chunk in order to bypass theunlink_chunkchecks. - We need to set the
PREV_SIZEof the next chunk such that the address of the next chunk minus the prev size gives you the location of the fake chunk. - Once these steps are done you can go ahead and free the victim chunk which will lead to consolidation and a pointer to your fake chunk being returned.
- One way to leverage this mechanism is to get overlapping chunks using the fake chunk over the chunk used to set the
PREV_INUSEbit. - This can be used to execute a TCache Poisoning attack to get arbitrary write.
Example Challenges
This post is licensed under CC BY 4.0 by the author.